Deployment Monitoring
Tool in SCCM 2012 Toolkit
Deployment Monitor Tool (DeploymentMonitoringTool.exe) is new addition to SCCM 2012 Toolkit. This Tool is a graphical user interface designed to assist in troubleshooting applications, updates and
baseline deployments.
The use of this tools comes with below
features.
1.
Actions
2.
Client Properties
3.
Deployments
4.
All Updates
Deployment Monitoring
Tool MUST be run as administrator.
Through actions menu
you can perform the following task
(a) Connect to A remote
Computer,
(b) Import and Export XML
files of a system for further troubleshooting
(c) Review the log files depending upon
which TAB are selected. For Example if it is Application and Baseline Deployments Tab –> PolicyAgent.log:, Update Deployments –>
updatesDeployment.log and All Updates
Tab –> WindowsUpdate.log:
Ø Client Properties
Client Properties tab
will help us to get all the client details. The following information is very
helpful at the time of troubleshooting. Client Logs Directory, ccmexec service Status, Service
Window (maintenance window) status, Proxy MP, Resident MP details, WSUS
Locations, Update Sources, Last Policy refresh Cycle,Assigned MP, Site Code,
Client Approved status and certificate information.
Ø Deployments
Deployments tab will
help us to list down the details of each targeted deployments.
This will provide us more details of the
deployments like Name, Deadline, State,Type and ID.
For example, in the
following pic, you can see the deployed application is OPTIONAL, state of deployment is APP_CI_ASSIGNMENT_EVALUATION, Deployment ID and
Deployment Type is Application. However, if you look at other two deployments, you can see that
one is Software Update and other one is mandatory application
deployment with a deadline.
We will get in depth characteristics of selected deployment in the bottom of the tool.
Information which can be fetched are as under.
These details are very very helpful at the time of troubleshooting.
1. AssignmentAction,
2. DisableMomAlerts,NotifyUser,
3. SuppressReboot,
4. OverrideServiceWindows,
5. RaiseMomAlertOnFailure,
6. StartTime, StartTime,
7. Target,
8. RebootOutsideOfServiceWindows,
9. UserUIExperience,
10. DeploymentType,
We can retrive
in-depth details about selected deployment at the bottom (each and every details that you’ve specified at the time
of creation of new application). For example – Properties (as mentioned above), Policy, Evaluation,
Content, Enforcement, Reporting and Requirement Violations.
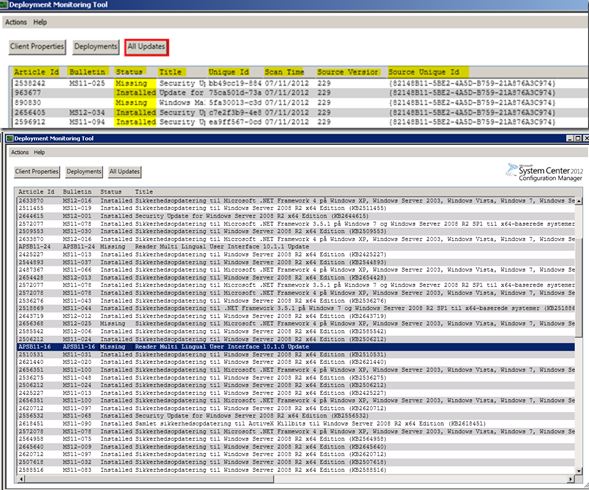
Ø All Updates
All updates tab will
provide the details about all the required updates along with their status.
Article ID, Bulletin, Status, Title, Unique ID, Scan Time, Source
Version and Source Unique ID